Varzia provides risk assessment service as a key component of a holistic, organization-wide risk management process. Risk management processes include:
Framing risk;
Assessing risk;
Responding to risk;
Monitoring risk.
Figure below illustrates the four steps in the risk management process—including the risk assessment step and the information and communications flows necessary to make the process work effectively.
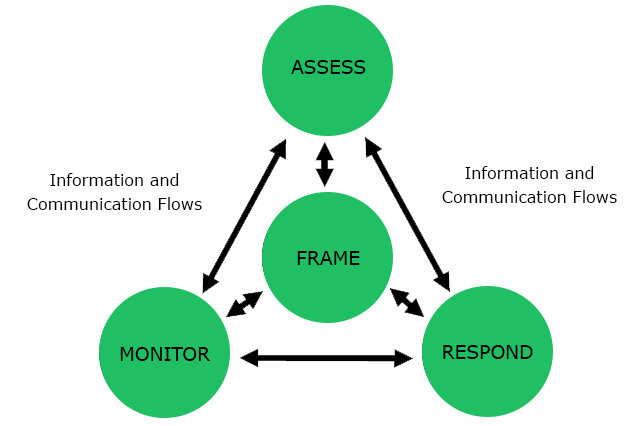
First stage of the risk management process in the organization is a risk assessment. Organizations conduct risk assessments to determine risks that are common to the organization’s core missions/business functions, mission/business processes, mission/business segments, common infrastructure/support services, or information systems. Risk assessments can support a wide variety of risk-based decisions and activities by organizational officials across all tiers in the risk management hierarchy.
The risk assessment process is composed of four steps:
(1) prepare for the assessment;
(2) conduct the assessment;
(3) communicate assessment results;
(4) maintain the assessment.
Each step is divided into a set of tasks. The figure below shows the process.
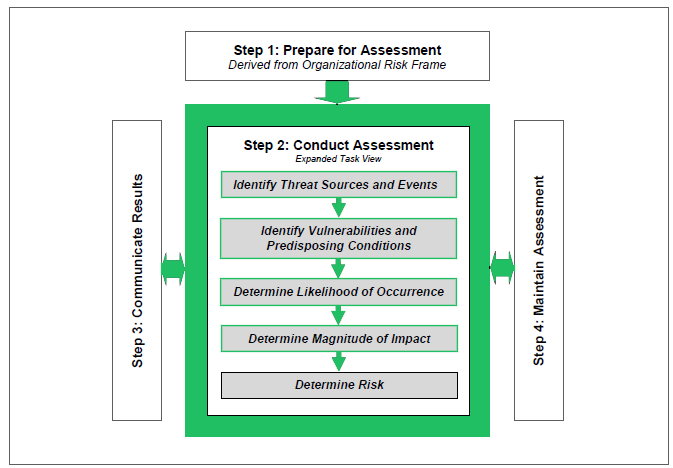
Conducting risk assessments includes the following specific tasks:
- Identify threat sources that are relevant to organizations;
- Identify threat events that could be produced by those sources;
- Identify vulnerabilities within organizations that could be exploited by threat sources
through specific threat events and the predisposing conditions that could affect
successful exploitation;
- Determine the likelihood that the identified threat sources would initiate specific threat
events and the likelihood that the threat events would be successful;
- Determine the adverse impacts to organizational operations and assets, individuals,
other organizations, and the Nation resulting from the exploitation of vulnerabilities by
threat sources (through specific threat events);
- Determine information security risks as a combination of likelihood of threat
exploitation of vulnerabilities and the impact of such exploitation, including any
uncertainties associated with the risk determinations.
